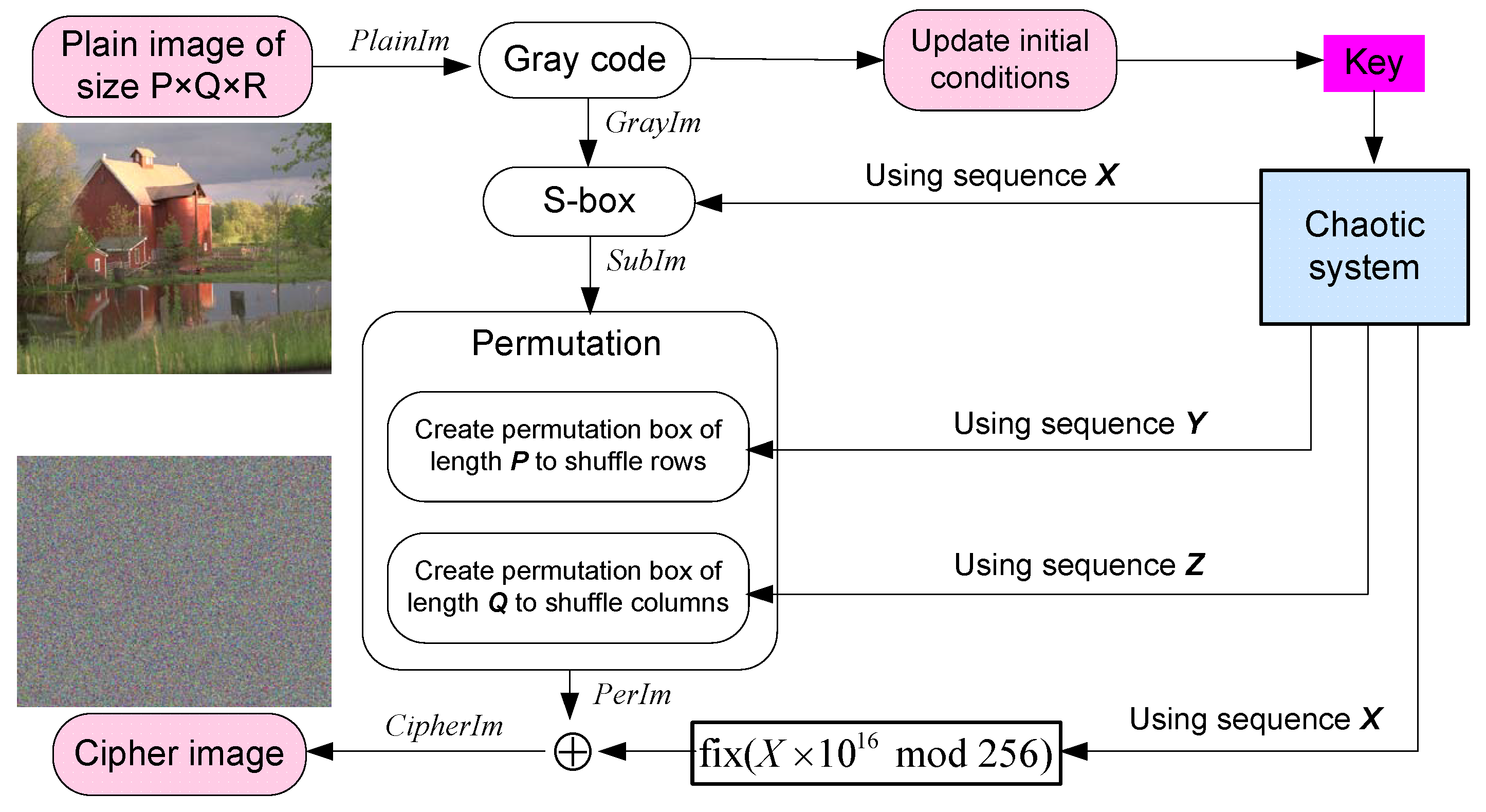
Electronics | Free Full-Text | Efficient Chaos-Based Substitution-Box and Its Application to Image Encryption | HTML
![POS system with white box encryption key sharing Patent Grant Murray February 2, 2 [Clover Network, Inc.] POS system with white box encryption key sharing Patent Grant Murray February 2, 2 [Clover Network, Inc.]](https://uspto.report/patent/grant/10909532/US10909532-20210202-D00003.png)
POS system with white box encryption key sharing Patent Grant Murray February 2, 2 [Clover Network, Inc.]

Buy Super Security Safe Deposit Box Anti-theft Lock With Encryption Keys Copper Cylinder at affordable prices — free shipping, real reviews with photos — Joom

Buy Super Security Safe Deposit Box Anti-theft Lock With Encryption Keys Copper Cylinder at affordable prices — free shipping, real reviews with photos — Joom




/cdn.vox-cdn.com/uploads/chorus_asset/file/3395694/Box_EKM_Encryption_Flow.0.png)





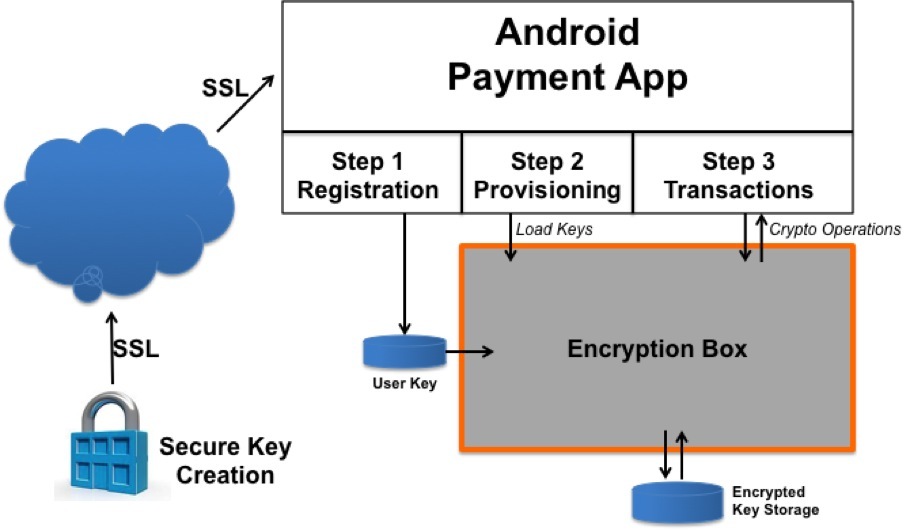







![KB7407] Encrypting and Decrypting Folders KB7407] Encrypting and Decrypting Folders](https://support.eset.com/storage/IMAGES/en/8348_KB7407/KB19_Folder_Wizard.png)


